Is your business confined to your physical storefront now?
No, right!
Similarly, your organization’s threat landscape is no more confined to a controlled network or your workforce devices!
In today’s fast-paced digital world, employees access the organizational data wherever they are. By embracing the hybrid work culture, organizations have expanded their security perimeters beyond their controlled network and migrated their on-premises infrastructure to cloud solutions.
All these digital transformation journey demanded a robust security model that combats the vulnerabilities of modern infrastructure & hybrid work culture to protect people, devices, endpoints, and data wherever they are!
And that’s when organizations moved to “Zero Trust Security Model”- a perimeter-less security architecture!
In this blog post, let’s explore Zero Trust Security Fundamentals and how it complements your organization’s enhanced cyber security posture!
Continue Reading
Zero Trust Security Fundamentals
Zero Trust Security model abides by the policy,
“Never Trust, Always Verify”!
Zero Trust Security architecture always presumes breach and verifies every accessibility request as it originates from an open or unknown network regardless of where, who or what resource is being accessed. With this security model, organizations are set to ensure accessibility of the right data at the right time for valid business purposes by the right people. On top of these precursors, Zero Trust leverages rich intelligence on behavioral patterns to mitigate anomalies in real-time.
Now, let’s discuss the three key areas to encapsulate in your Zero Trust Security Framework!
Employees/Workforce
As of now, the majority of organizations have a hybrid infrastructure of on-premises & cloud environments. Either they’re in the process of modernization or retaining the on-premises infrastructure for some of their confidential endpoints.
Considering this complex IT infrastructure setup, it’s proposed to shift to cloud-based identity solutions to strengthen your organization’s security posture!
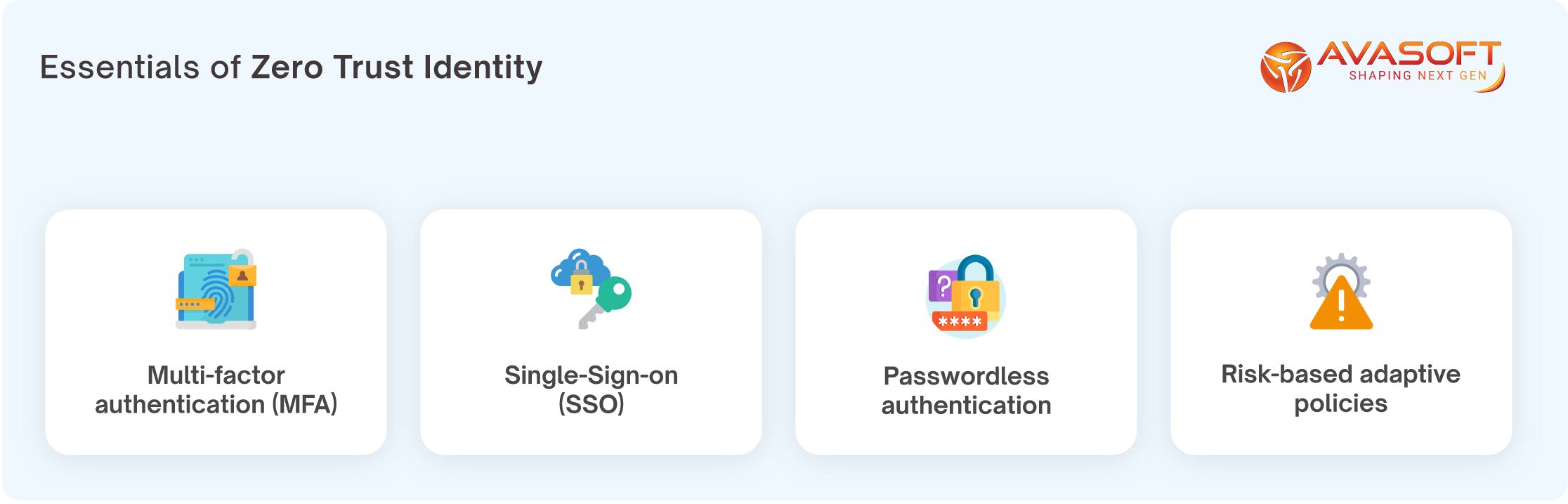
Zero trust identity involves these stages:
- Validating user identity & devices
- Monitoring user behavioral patterns
- Implementing adaptive policies
Endpoints/Workloads
Upon granting access to your organizational assets, you need to ensure the simplicity and security of the endpoint accessibility. The excessive privilege to a particular user identity creates a massive threat to the digital space of your organization.
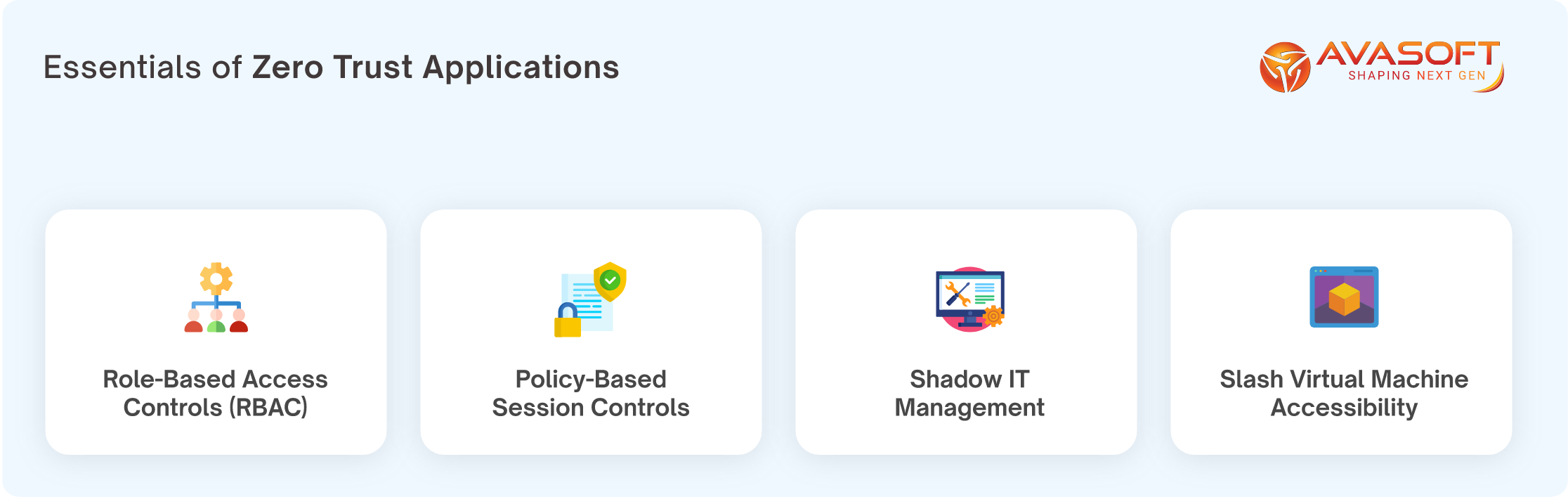
Implementing Zero Trust Endpoint involves:
- Employing policies and micro-segmentation to explore Shadow IT.
- Ensuring least-privileged access management with real-time analytics.
- Monitoring behavioral patterns & restrict abnormal user actions.
- Validating security configurations at regular intervals.
Environment/Workplace
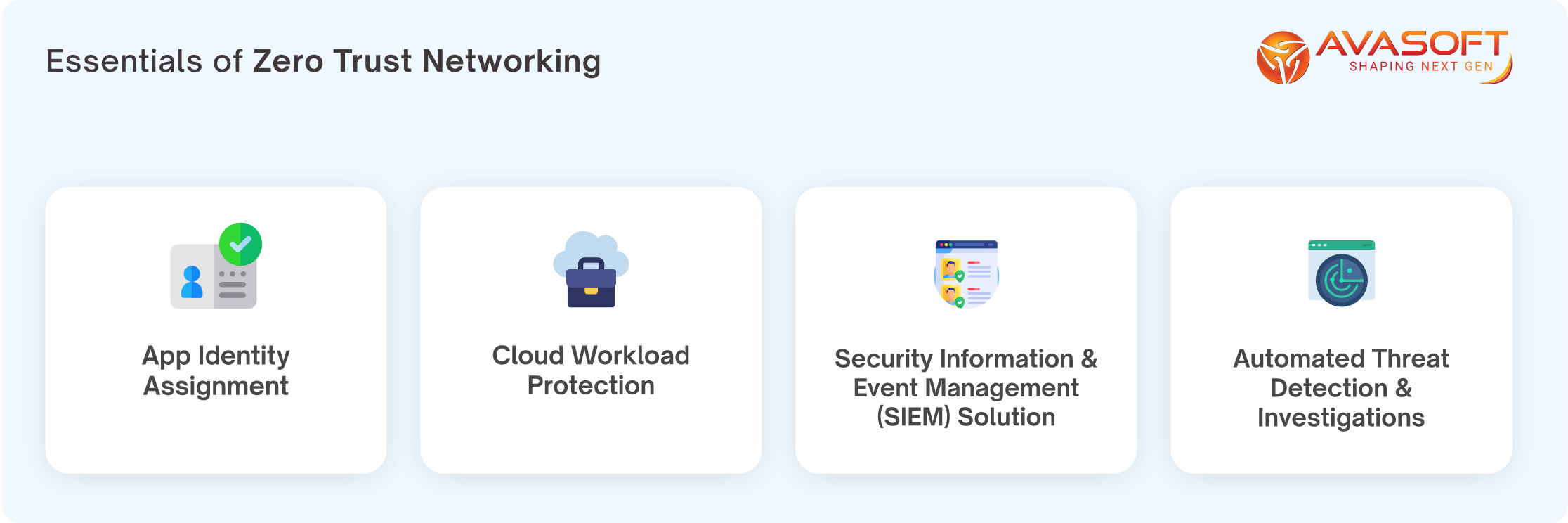
Be it an identity or application threat, it’s accessed over the network. Unfolding the vulnerabilities inside and beyond your organizational perimeter is paramount in this digital realm.
If your organization has a flat & open network with a minimal & unencrypted threat landscape, it’s time to re-engineer your network architecture!
- Mitigate security perils proactively.
- Minimize the blast radius and vulnerability inflation.
- Increase the roadblocks to attain your organizational footprint.
Wrapping up!
In the world of overwhelming digital assets, breaches are inevitable!
But then your robust security practices do make a difference in mitigating and reducing the severity of cyber exposure and security debts.
Adopting a 360-degree Zero Trust Security Model is great for every organization! However, the security challenges of every organization depend on threat patterns, business needs, and capabilities. This can be directly proportional to your unique Zero Trust Security journey!
Our team can assess the Zero Trust maturity stage of your organization and propose & implement the customized security architecture to elevate your organization’s cyber security from good to great!

